Securing Wireless Communication in Critical Infrastructure: Challenges and Opportunities
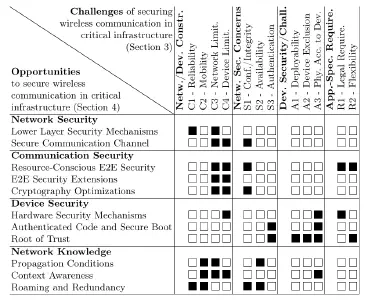
Critical infrastructure increasingly relies on wireless communication, transitioning from dedicated private wired networks to heterogeneous wireless systems. This shift introduces unique security challenges due to the use of public/shared networks and resource-constrained devices. The paper systematically identifies key challenges in reliability, mobility, network/device limitations, and security requirements, while proposing a comprehensive set of solutions including lower-layer security mechanisms, end-to-end security optimizations, hardware-based device security, and context-aware network adaptation strategies. The work provides a structured taxonomy of security challenges across four dimensions (network/device constraints, network security concerns, device security challenges, and application-specific requirements) and maps them to concrete mitigation opportunities. Experimental insights and case studies demonstrate how combining multiple security approaches can address the inherent trade-offs between security, reliability, and resource constraints in modern critical infrastructure deployments.