Autarke Breitbandnetze Im Katastrophenfall Forschung auf dem Summer Breeze Open Air
Ein Metal-Festival als Testumgebung für ein Forschungsprojekt? Was auf den ersten Blick ungewöhnlich erscheint, war für das Team des Forschungsprojekts 5G-Opportunity eine einmalige Gelegenheit, um auf dem Summer Breeze Open Air 2024 die Forschungsergebnisse für eine innovative Kommunikationslösung im Zivil- und Katastrophenschutz zu erproben. Gemeinsam mit dem Malteser Hilfsdienst konnten die Einsatzabschnittsleitungen zuverlässig über WLAN-Richtfunk miteinander verbunden werden. Um auch auf dem Festivalgelände selbst den mobilen Einsatzkräften einen Netzzugang zu bieten, wurde eine Kombination aus WLAN- und 5G-Access verwendet. Ein zentrales Forschungsziel war der flexible Einsatz von 5G-Frequenzen: Freies Spektrum sollte vor Ort mit speziellen Messgeräten erkannt werden, um dann opportunistisch genutzt werden zu können.
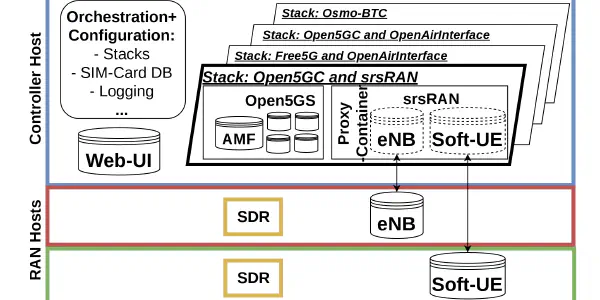
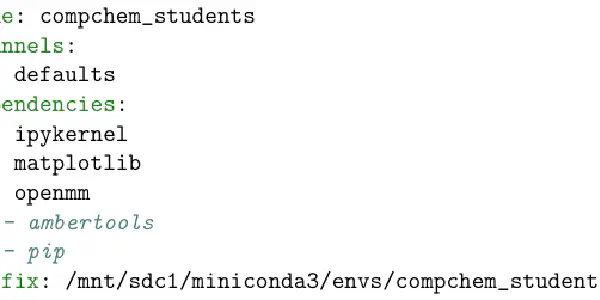
open5Gcube: A Modular and Usable Framework for Mobile Network Laboratories
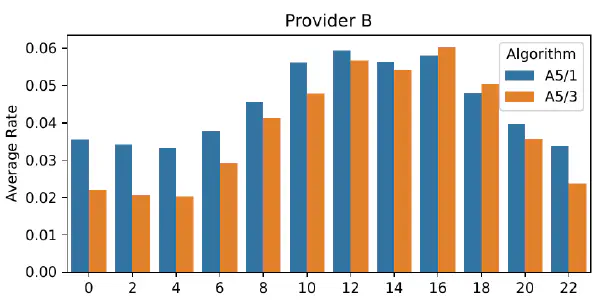
A5/1 is in the Air: Passive Detection of 2G (GSM) Ciphering Algorithms
Adaptive Optimization of TLS Overhead for Wireless Communication in Critical Infrastructure
With critical infrastructure increasingly relying on wireless communication, using end-to-end security such as TLS becomes imperative. However, TLS introduces significant overhead for resource-constrained devices and networks prevalent in critical infrastructure. In this paper, we propose to leverage the degrees of freedom in configuring TLS to dynamically adapt algorithms, parameters, and other …
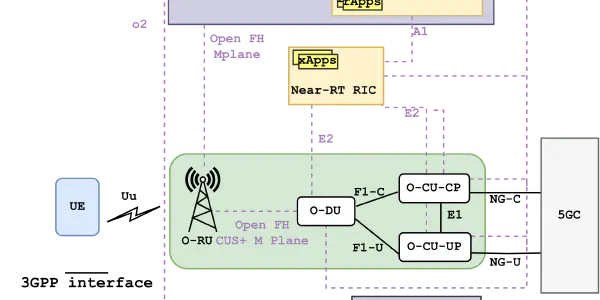
Open RAN: A Concise Overview
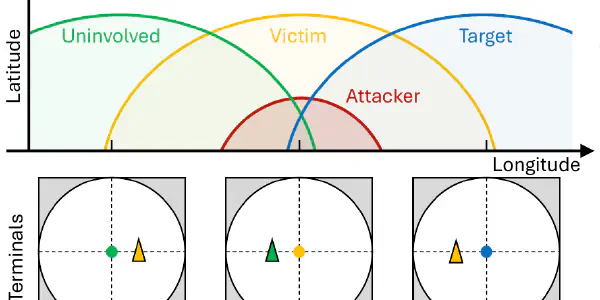
Dude, Where’s That Ship? Stealthy Radio Attacks Against AIS Broadcasts
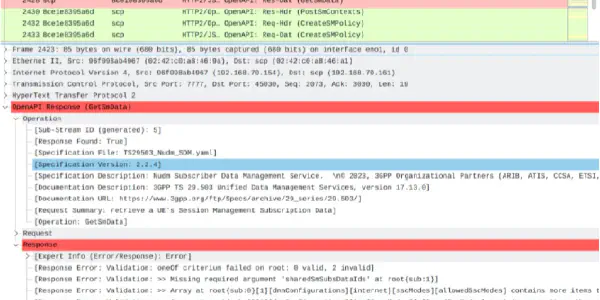
Implementation of OpenAPI Wireshark Dissectors to Validate SBI Messages of 5G Core Networks
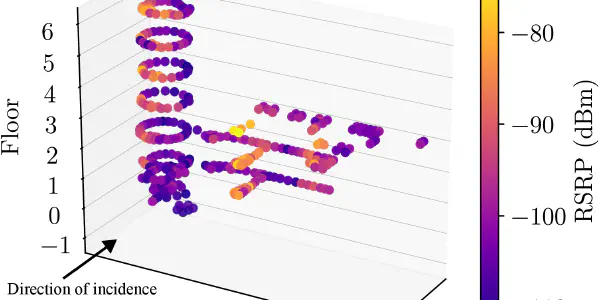
Measurements of Building Attenuation in 450 MHz LTE Networks

Security Vulnerabilities in 5G Non-Stand-Alone Networks: A Systematic Analysis and Attack Taxonomy
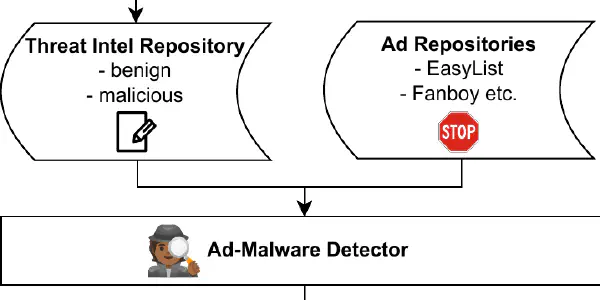
Utilizing DNS and VirusTotal for Automated Ad-Malware Detection
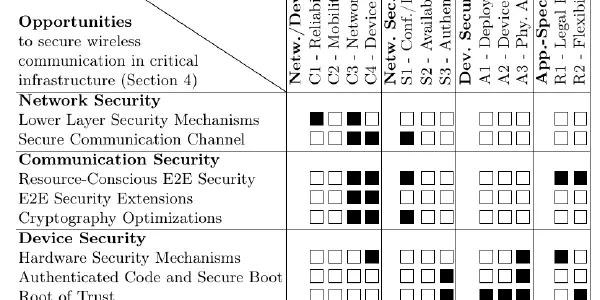
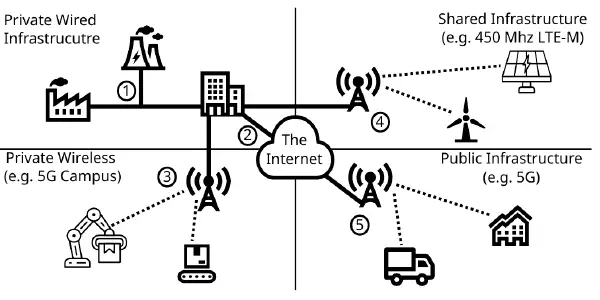
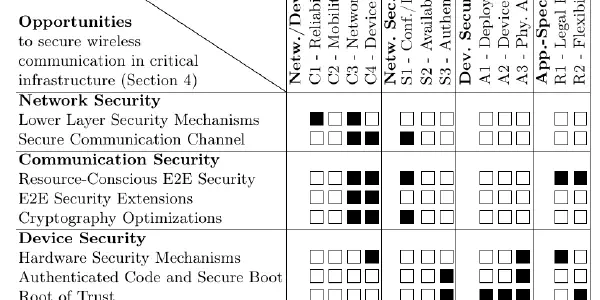
Securing Wireless Communication in Critical Infrastructure: Challenges and Opportunities
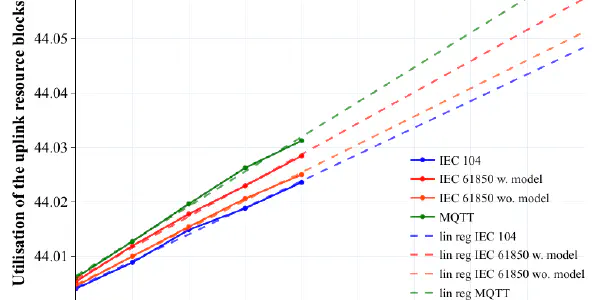
A Modular Framework for Evaluating Smart Grid Communication Protocols over Mobile Networks
Katti: An Extensive and Scalable Tool for Website Analyses
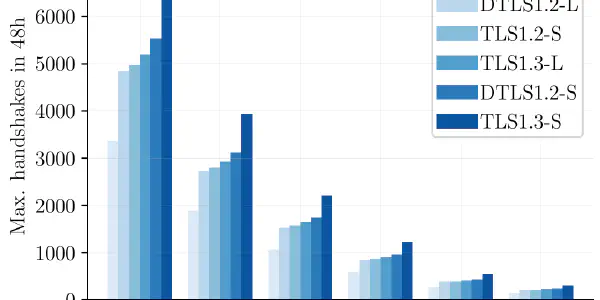
Bounds for the Scalability of TLS over LoRaWAN
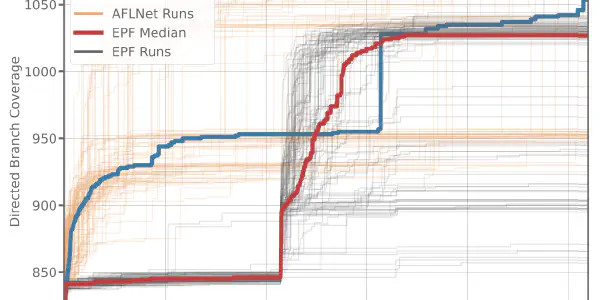
EPF: An Evolutionary, Protocol-Aware, and Coverage-Guided Network Fuzzing Framework
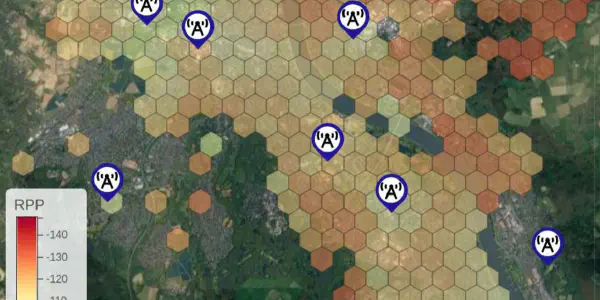
Path Loss in Urban LoRa Networks: A Large-Scale Measurement Study
Urban LoRa networks promise to provide a cost- efficient and scalable communication backbone for smart cities. One core challenge in rolling out and operating these networks is radio network planning, i.e., precise predictions about possible new locations and their impact on network coverage. Path loss models aid in this task, but evaluating and comparing different models requires a sufficiently …